How to Ensure Cloud Compliance for Financial Data

Financial firms face complex regulations when storing sensitive data in the cloud. Key laws like GLBA, SOX, PCI DSS, SEC, and FINRA impose strict requirements for protecting customer data, trading records, and financial reporting systems. Non-compliance risks include fines, operational disruptions, and reputational damage.
Here’s what you need to know:
- Identify regulations: Match your business activities to laws like SEC Rule 17a-4 (WORM storage for trading records) or PCI DSS (payment card data encryption).
- Classify data: Map datasets to regulatory requirements (e.g., cardholder data under PCI DSS, loan files under GLBA).
- Choose the right cloud provider: Look for SOC 1/2, ISO 27001 certifications, and U.S.-only data storage options.
- Build compliant cloud architecture: Use encryption, segmented networks, and IAM controls to meet regulatory standards.
- Monitor continuously: Use tools like CSPM and SIEM to enforce policies, detect misconfigurations, and log activities.
- Align with financial operations: Integrate cloud compliance into SOX controls, vendor management, and board reporting.
Pro tip: Continuous monitoring and detailed compliance registers simplify audits and reduce risks. Partnering with experts can streamline the process for growth-stage firms.
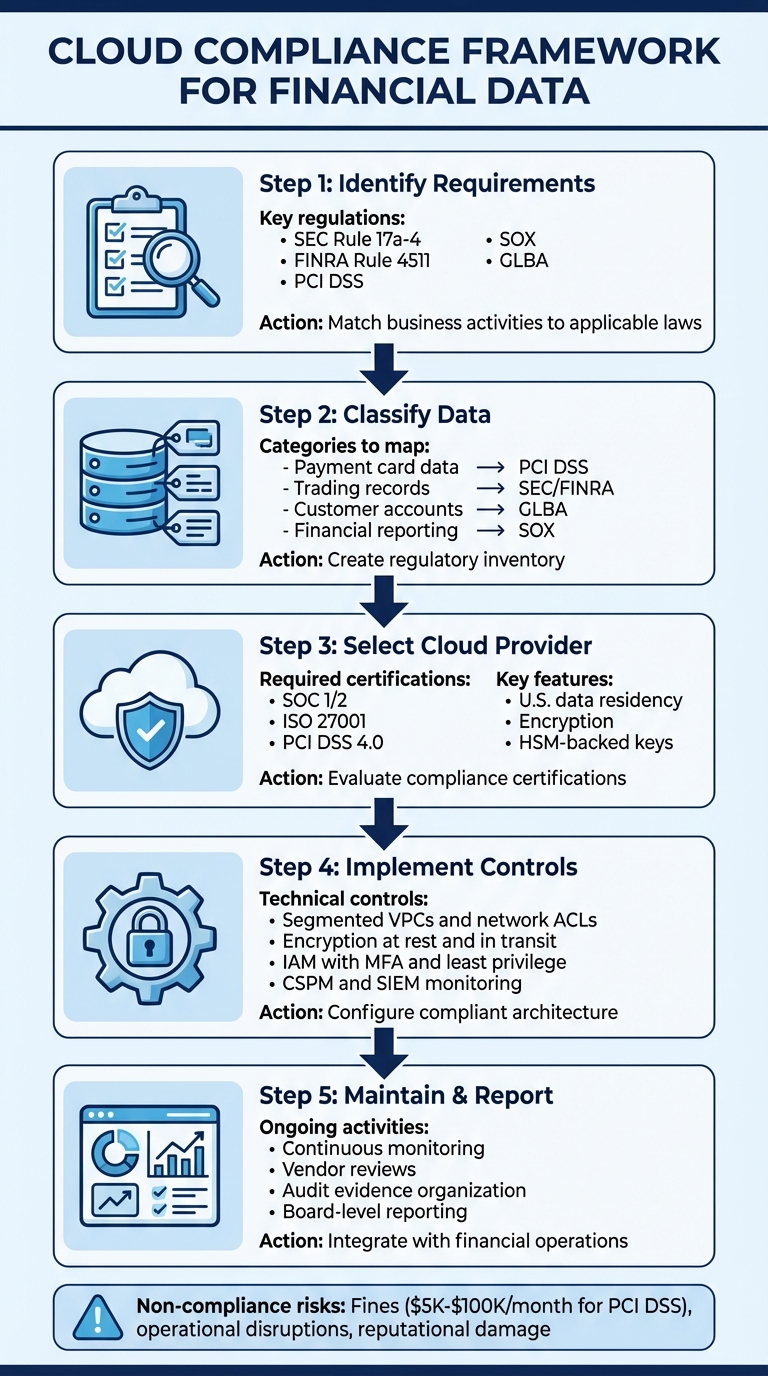
5-Step Cloud Compliance Framework for Financial Data
Cloud Compliance and Security in the Financial Industry
Identify Your Compliance Requirements
Start by matching your business activities to the relevant U.S. regulations. For example, if you're a broker-dealer, your recordkeeping practices fall under SEC Rule 17a-4 and FINRA Rule 4511. These rules require you to store trading records, order tickets, and client communications in non-rewritable, non-erasable (WORM) formats, with retention periods ranging from three to six years. If your business deals with credit or debit card transactions, PCI DSS sets strict standards for encrypting cardholder data, segmenting networks, and maintaining detailed logs. Public companies must comply with SOX for financial reporting systems, while firms handling customer account information must follow GLBA to safeguard nonpublic personal data. The sections below break down key regulations, methods for classifying data, and how to turn these requirements into actionable cloud controls.
U.S. Regulations That Apply to Financial Data
The first step is identifying which regulations govern your data. For instance, SEC Rule 17a-4 requires broker-dealers to preserve electronic records in tamper-proof formats, maintain accurate indexes, and ensure quick access for regulators. This often involves using object lock or WORM storage, geographically redundant backups, and clear retrieval procedures. FINRA Rule 4511 reinforces these obligations and adds an important caveat: outsourcing to a cloud provider doesn’t shift your regulatory responsibilities. You must still oversee vendor performance, review SOC reports, and confirm that retention settings align with regulatory requirements.
If you handle payment card data, PCI DSS applies. Non-compliance can result in fines ranging from $5,000 to $100,000 per month, depending on your transaction volume and how long violations persist. Beyond financial penalties, card brands may restrict your access to payment networks, effectively halting card transactions. Many organizations also adopt frameworks like NIST or ISO 27001 to establish internal security and privacy controls, especially when regulators or investors expect robust governance. Additionally, if your company manages health-related financial accounts like HSAs, HIPAA may indirectly influence how you secure combined health and financial data in the cloud.
Classify Your Financial Data by Regulation
Once you’ve identified the applicable regulations, the next step is to categorize your data and map it to specific requirements. Create an inventory that labels each dataset with its regulatory obligations. For example:
- Payment card data falls under PCI DSS and requires strong encryption, proper key management, and network segmentation.
- Trading records, order communications, and blotters are governed by SEC Rule 17a-3/4 and FINRA Rule 4511.
- Customer account statements and loan files are subject to GLBA protections for nonpublic personal information.
- General ledger and subledger data used in financial reporting must meet SOX internal control standards.
To ensure consistent mapping, ask key questions for each dataset: Does it include records tied to broker-dealer activities? Does it contain cardholder data subject to PCI DSS? Is it part of financial reporting under SOX? Does it include personal information protected by GLBA? Document the origin of the data, where it’s stored, and any third-party access. This detailed mapping helps ensure regulated data stays in approved locations and prevents non-compliant copies from being created through backups, logs, or analytics outputs.
Document Requirements in a Compliance Register
Turn regulatory obligations into actionable cloud controls by organizing them in a compliance register. Break down each regulation into cloud-specific requirements. For instance:
- SEC Rule 17a-4 and FINRA Rule 4511: Require WORM storage, indexability, quick retrieval, and regulator access.
- PCI DSS: Enforces encryption, network segmentation, vulnerability management, and detailed logging.
- SOX: Calls for strict access controls, change management, and audit trails for financial systems.
- GLBA: Requires safeguards like encryption to protect customer information.
For each requirement, link it to specific cloud controls and assign responsibility. For example, map "WORM retention for trade confirmations" to your cloud provider’s object lock feature, document the setup, and assign a compliance officer to regularly verify these configurations. Use your cloud provider’s compliance resources to confirm certifications like SOC 2, ISO 27001, or PCI DSS. Keep your compliance register up to date by integrating it with tools like configuration management databases, data catalogs, or automated discovery systems that track changes in your cloud environment.
Select and Configure Your Cloud Provider
When selecting a cloud provider, it’s crucial to ensure they meet your regulatory requirements. Look for SOC 1 Type II and SOC 2 Type II reports, along with ISO/IEC 27001 certification. Additionally, confirm they comply with ISO 27017 and ISO 27018, which address cloud-specific security and the protection of personally identifiable information (PII) [7][4][8]. If your organization processes payment cards, verify that the provider supports PCI DSS 4.0 compliance. This includes documented responsibility matrices and validated PCI-eligible services [4]. Once these certifications are confirmed, align the provider's offerings with your specific regulatory requirements. Finally, evaluate how effectively the provider implements these controls in practice.
Evaluate Providers Based on Compliance Certifications
Take a close look at audit reports and penetration test summaries to assess critical areas like logging, access control, encryption, and business continuity. For U.S. financial institutions, these documents are essential for meeting obligations under Regulation S-P, FINRA cybersecurity expectations, the GLBA, and SEC guidance [9][5]. Beyond certifications, confirm that the provider supports U.S.-only data storage for regulated information. Be sure to examine how backups, logs, analytics outputs, and failover replicas are handled to avoid unintentional cross-border data replication, which could violate data residency rules. Additionally, review the provider’s policies for law enforcement requests and transparency reports to understand how the U.S. CLOUD Act might impact your data. To mitigate risks of unauthorized cross-border access, consider using customer-managed encryption keys stored on U.S. hardware security modules (HSMs) [5].
Set Up Cloud Architecture for Compliance
After selecting a provider, configure your cloud environment to enforce compliance with regulatory requirements. Start by designing segmented virtual private clouds (VPCs) with specific subnets and network access control lists (ACLs) for production, non-production, and management workloads. Use a least-privilege approach to restrict traffic [9][10]. For systems handling sensitive financial or payment data, create isolated network segments [9][10]. Ensure encryption is enabled by default across all workloads, using tools that meet PCI DSS 4.0 standards [9][4]. For highly sensitive data under GLBA - such as account numbers, trading records, or PII - leverage customer-managed keys (CMKs) or HSM-backed keys to maintain control over key generation, rotation, and revocation [4][5].
To enhance access control, implement identity and access management (IAM) with least-privilege roles, multi-factor authentication (MFA), and role-based access control for both users and service accounts. Log all administrative actions for accountability [9][7]. For remote or partner access, opt for private connectivity options rather than exposing management interfaces to the public internet. Centralize authentication through directory services designed to meet the financial sector's strong authentication requirements [9][4]. Compare these technical configurations across providers to ensure they meet your compliance needs.
Compare Provider Compliance Features
Create a matrix to evaluate providers based on key criteria such as compliance certifications (SOC 1/2, ISO 27001/27017/27018, PCI DSS participation), U.S. data residency options, encryption and key management capabilities, network security features, logging and monitoring depth, third-party risk management, and cost considerations like native security tools and log storage [7][10]. Use a weighted scoring model to prioritize regulatory-critical features like data residency controls and encryption. Assign moderate weights to integration and tooling capabilities, and lower weights to secondary features.
To make this process more actionable, include example scenarios in your evaluation - such as how each provider would handle a PCI DSS cardholder data environment or an SEC-regulated trading platform. This approach ensures the provider’s features align with your operational needs. By quantifying trade-offs, you can rank providers effectively. For additional guidance, consider collaborating with specialized financial advisors like Phoenix Strategy Group to ensure your cloud configurations meet both investor and regulatory expectations for auditability and reporting.
sbb-itb-e766981
Implement Daily Compliance Operations
Incorporating compliance into your daily operations is essential. Start by establishing clear policies for system access, data retention, and incident response. Regular monitoring helps catch misconfigurations early, preventing them from escalating into audit issues. The financial services industry has shifted from annual compliance checks to continuous compliance, thanks to tools that scan configurations in real time and enforce policies as code [4][7]. These practices ensure that your operations consistently align with regulatory requirements.
Create Standard Policies and Controls
Set up formal policies to manage changes and configurations, particularly for infrastructure-as-code (IaC). These policies should outline how changes to cloud networking, IAM roles, and storage configurations are approved, tested, and deployed. This approach supports SOX internal control requirements and SOC 2's "Change Management" standards [2][7]. Clearly define who can approve production changes and implement segregation of duties (SoD) to ensure no single person can both develop and deploy changes to production systems. To enforce SoD, use separate cloud accounts or projects for development, testing, and production environments [2][4].
Add an extra layer of security with just-in-time (JIT) elevation for administrative access. This involves time-limited role elevation through an approval workflow, with automatic logging of actions. It minimizes standing privileges while strengthening your SOC 2 and PCI DSS compliance [2][7]. For data protection, document your policies for data retention, backup, and disaster recovery. Develop a robust incident response policy that covers severity levels, playbooks, notification triggers for regulators, and steps for preserving evidence. These measures align with GLBA, PCI DSS, and NIST standards [2][4].
Monitor Compliance Continuously
Once your policies are in place, focus on real-time monitoring to maintain compliance. Cloud Security Posture Management (CSPM) tools can scan for misconfigurations, while a SIEM platform centralizes logs for real-time alerts and audit trails. Map CSPM rules to regulatory frameworks like PCI DSS, SOC 2, ISO 27001, and GLBA to ensure findings are directly tied to compliance requirements [2][7]. Centralize logs from systems and applications, including OS logs, database audit logs, web server logs, and API gateway logs. Set up alerts for suspicious activities like failed logins, privilege escalations, unusual data exports, or changes to security groups and firewalls [2][4][7].
Use DLP or data discovery tools to flag unauthorized transfers of financial data or personally identifiable information (PII) to external platforms or unapproved SaaS tools [3][6][7]. Track daily metrics such as critical security alerts, triage times, open misconfigurations by severity, and logging coverage across systems. Share summaries of these metrics with compliance and risk teams regularly [4][7]. Ensure clock synchronization across all cloud resources using NTP to maintain consistent timestamps in logs - this is critical for investigations and regulatory reviews [2][7].
Conduct regular vulnerability scans and penetration tests, including assessments specific to cloud environments. Track remediation timelines to meet internal and regulatory expectations [2][7]. Develop a detailed incident response playbook with clear roles, escalation paths, notification timelines, and evidence collection procedures. Schedule annual tabletop and technical exercises to test and refine your response strategies [2][4].
Organize Evidence for Audits
Daily compliance efforts need to be well-documented and audit-ready. Create configuration baselines - such as "golden images" and hardened templates - for financial workloads, and use configuration management tools to monitor and fix any deviations [2][4][7]. Maintain comprehensive audit logs to track system activities and changes, providing an immutable record for compliance verification [1]. Preserve a detailed history of data to support retention policies and provide evidence for regulatory audits [1].
Organize evidence by control domains like access management, encryption, logging, and incident response. Map each piece of evidence to specific regulatory requirements, such as GLBA, SOX, PCI DSS, or SOC 2. Use version control for policy documents and securely store audit reports, penetration test summaries, and compliance certifications in a centralized repository with restricted access. Implement advanced permissions to tightly control who can access sensitive financial data and cloud resources. Use SSO/SAML authentication to enhance security and streamline user access [1]. Centralizing audit evidence not only supports continuous compliance but also simplifies audit preparation and ensures leadership has a clear view of compliance efforts.
Connect Compliance to Financial Operations
Cloud compliance isn’t just an IT issue - it needs to be tightly woven into your financial workflows, vendor management processes, and governance reporting. When compliance operates in isolation from financial controls, gaps can arise between what your cloud systems provide and what your financial operations demand. The goal is to integrate compliance seamlessly into your finance team’s processes, from vendor oversight to board-level reporting. Here’s how you can evaluate vendors, embed regulatory controls into financial operations, and communicate effectively with leadership.
Review Third-Party Vendors for Compliance
Every cloud provider or SaaS tool that interacts with your financial data becomes a part of your compliance ecosystem. Under U.S. regulations like the Gramm-Leach-Bliley Act (GLBA) and FINRA rules, your organization remains accountable for compliance - even when certain functions are outsourced [12]. Start with a formal vendor due diligence process to assess each provider’s regulatory alignment before signing contracts. Request SOC 1 Type II and SOC 2 Type II reports for vendors handling financial data [13]. For payment processors, confirm they meet PCI DSS standards and check for certifications such as ISO 27001 or FedRAMP authorization when relevant.
Make sure contracts include clear clauses on data residency and sovereignty, specifying where financial data is stored, how cross-border transfers are managed, and how regulatory examinations are handled [11]. Vendor contracts should directly align with documented regulatory requirements. Treat vendor oversight as an ongoing responsibility by conducting annual certificate reviews, periodic security questionnaires, and regular SLA performance evaluations. Document these activities thoroughly to prepare for audits.
Once your vendors meet compliance standards, the next step is aligning your cloud controls with your financial reporting processes.
Integrate Compliance with Financial Controls
After establishing cloud controls, connect them to your financial reporting systems. These controls should align directly with SOX (Sarbanes-Oxley Act) objectives, especially for systems that impact the general ledger or financial statements [13]. Identify which cloud services are tied to financial reporting and ensure key controls - like identity and access management, logging, encryption, backups, and change management - meet SOX requirements. Maintain a clear separation of duties by keeping development, testing, and production roles distinct to protect financial data.
Introduce a structured change management process for updates to financial applications or cloud infrastructure, ensuring it aligns with SOX objectives. Use cloud-native tools such as AWS Config, CloudTrail, or Google Cloud Audit Logs to create immutable audit logs that track access, configuration changes, and data movement - essential evidence for SOX and IT general controls [14]. Additionally, align your backup, disaster recovery, and business continuity plans with financial close and reporting schedules. Track compliance metrics and exceptions in a financial risk register, and have finance and internal audit teams review it jointly.
Report Compliance Status to Leadership
Regular updates to audit committees, risk committees, and boards are essential for effective governance [12]. Create a standardized cloud risk and compliance dashboard that provides an overview of your posture against key regulations - such as SOX, PCI DSS, GLBA, FFIEC, and SOC 2. Highlight high-risk vendors with unresolved issues and document any incidents or outages affecting financial data. Use a straightforward risk rating system (e.g., red, amber, green) and assign clear remediation responsibilities.
Include risks like data residency violations, SaaS outages during critical reporting periods, or misconfigured storage that exposes sensitive data in your enterprise risk management framework. Ensure joint updates are presented by your CFO, CIO, CISO, and compliance leaders, so leadership can see how cloud controls support financial integrity, regulatory compliance, and broader business goals. For growth-stage companies preparing for fundraising or an exit, financial advisory partners like Phoenix Strategy Group can help translate cloud and data risks into actionable financial metrics and board-level narratives - critical for investor due diligence, M&A readiness, and strategic planning.
Conclusion
Staying compliant in the cloud is an ongoing process that requires careful attention, regular updates to controls, and frequent reviews. Key actions include mapping financial data to relevant U.S. regulations like GLBA, PCI DSS, SOX, and SEC/FINRA rules, selecting cloud providers with proper certifications and robust data residency measures, implementing strict access management and monitoring, addressing third-party vendor risks, and aligning compliance efforts with financial governance and board-level reporting. These steps provide a clear framework for making meaningful progress.
For growth-stage companies, it’s crucial to plan for expenses related to logging, backups, and data residency while also meeting investor expectations. Advisory firms such as Phoenix Strategy Group can assist by integrating compliance with financial workflows, creating compliant data systems, and developing board-ready dashboards that translate technical risks into business insights investors can easily grasp.
FAQs
What regulations must financial firms follow when using cloud services?
Financial firms leveraging cloud services must navigate a range of regulations to ensure both data security and legal compliance. Among these are data residency and sovereignty requirements, which often mandate that sensitive information remains within U.S. borders. Firms are also obligated to comply with industry-specific laws and standards, such as the Gramm-Leach-Bliley Act (GLBA), the Sarbanes-Oxley Act (SOX), and the guidelines established by the Federal Financial Institutions Examination Council (FFIEC).
Carefully understanding and applying these regulations is critical for protecting financial data and staying compliant in cloud-based operations.
What steps can financial companies take to ensure their cloud providers comply with regulations?
Financial companies can safeguard regulatory compliance with their cloud providers by taking a few essential steps. Start by confirming that the provider has necessary certifications like SOC 2 or ISO 27001. These certifications indicate that the provider meets rigorous security and compliance standards, which are crucial in the financial sector.
It's also vital to define clear policies around data residency and sovereignty. This ensures that sensitive financial data is stored and processed only in approved jurisdictions, aligning with regulatory requirements.
Equally important is ongoing oversight. Regular audits and the use of real-time monitoring tools can help evaluate the provider’s compliance and security measures. Staying vigilant allows companies to reduce risks and maintain confidence in their cloud-based systems.
How can financial companies incorporate cloud compliance into their daily operations?
To make cloud compliance a natural part of your daily operations, begin by keeping your compliance policies up-to-date. Regularly review and adjust them to align with changing regulations. Automating tasks like data collection and reporting with secure tools can cut down on manual mistakes and boost efficiency. Keeping a close eye on data residency and sovereignty requirements is also essential to ensure you're meeting compliance standards.
It's equally important to train your team on compliance protocols so they clearly understand their responsibilities. Using compliance dashboards can give you real-time insights, allowing you to address potential issues before they escalate. For deeper expertise, partnering with trusted advisors who specialize in financial compliance and strategic planning can be a smart move. Their guidance can help you navigate complex regulations with confidence.