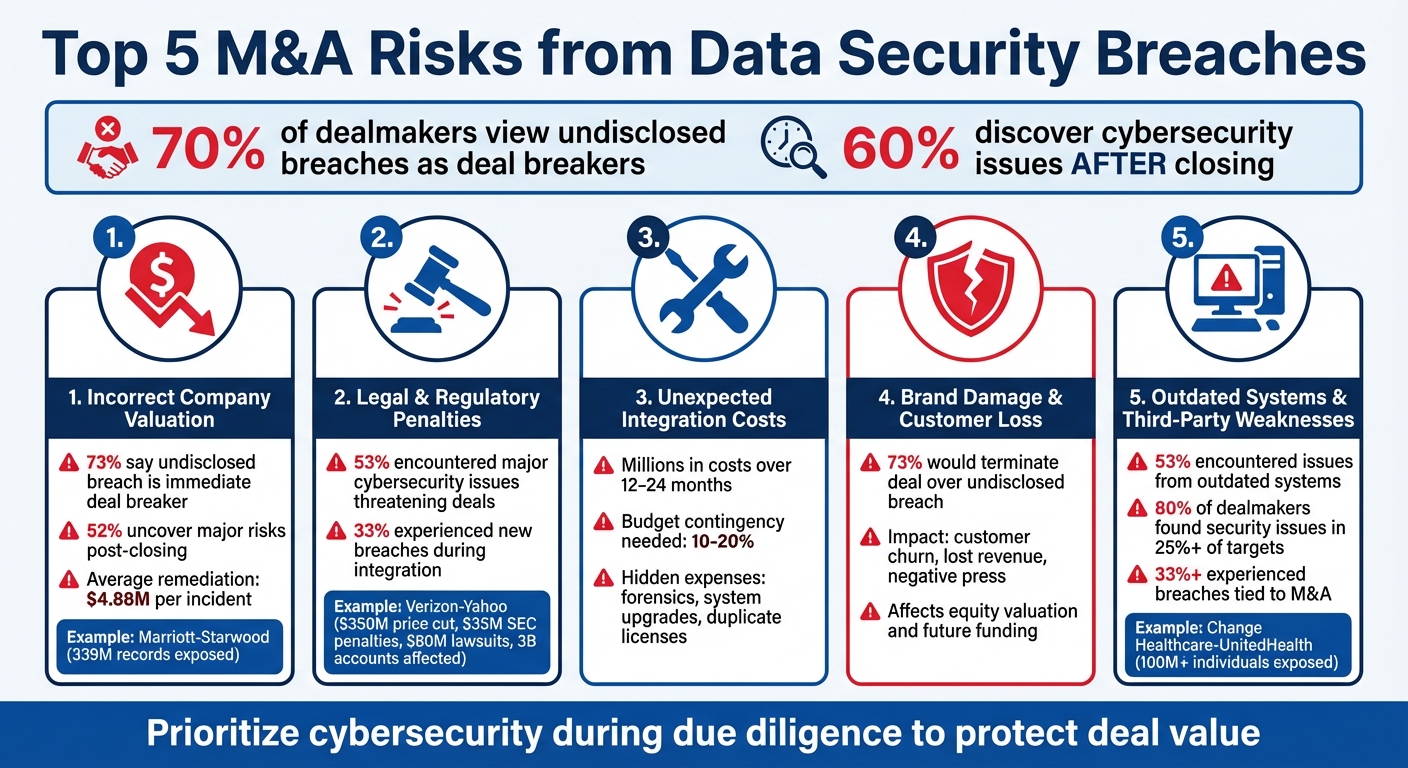
Top 5 M&A Risks from Data Security Breaches

When companies merge or acquire others, cybersecurity risks can create serious financial and reputational problems. Over 70% of dealmakers view undisclosed breaches as deal breakers, and 60% of companies only discover cybersecurity issues after closing a deal. These risks can lead to reduced valuations, unexpected costs, and legal troubles.
Here are the top 5 risks you need to know:
- Overpaying for a company due to hidden breaches, as seen in high-profile cases like Marriott-Starwood.
- Legal penalties from inherited breaches, such as Verizon's $350M price cut after acquiring Yahoo!.
- Surging integration costs to fix security gaps, which can run into millions over 1–2 years.
- Brand damage and customer trust loss, leading to revenue hits and negative media coverage.
- Outdated systems and vendor vulnerabilities, creating long-term security challenges.
To reduce these risks, prioritize cybersecurity during due diligence. Audit systems, assess breach histories, and evaluate vendor relationships. Use findings to adjust deal terms and plan for secure integrations. Ignoring these steps can cost millions and harm your reputation.
Top 5 M&A Cybersecurity Risks: Statistics and Financial Impact
Cybersecurity Risks in M&A | Valuation Impact, Incident Response & Best Practices
1. Incorrect Company Valuation
When a data breach is hidden within a target company, buyers often end up paying more than they should. On the surface, the financials might seem solid, but undisclosed security incidents can create unseen liabilities that chip away at the company's actual value. According to a Forescout survey, 73% of M&A professionals say an undisclosed data breach is an "immediate deal breaker" [2]. Unfortunately, many breaches only come to light after the deal is closed, leaving buyers to grapple with the fallout. These hidden issues can lead to severe and costly consequences.
Take the Marriott-Starwood acquisition as an example. A breach that began in 2014 went undetected for four years, ultimately exposing 339 million records. This oversight left Marriott facing regulatory fines, remediation expenses, and legal liabilities - all stemming from a breach that started long before the acquisition [3].
To avoid such risks, thorough technical assessments and forensic reviews are essential. Due diligence should include investigations into data storage, access controls, and any prior unauthorized access. For instance, one security review revealed a year-old breach confirmed by a law firm letter, which led the buyer to completely reassess the value of the deal [2].
The financial toll of these breaches can be staggering. On average, remediation costs alone amount to $4.88 million per incident [4]. Add to that potential regulatory penalties under laws like GDPR or CCPA, legal fees, and the loss of competitive advantage from stolen intellectual property, and the overvaluation risks become even clearer. Alarmingly, 52% of M&A deals uncover major cybersecurity risks during post-closing integration - after the purchase price has already been locked in [2].
To better align purchase prices with the true, risk-adjusted value of a company, strong cybersecurity due diligence is a must. This includes technical assessments, forensic log reviews, and vendor risk analyses to identify vulnerabilities before they escalate. Phoenix Strategy Group, for example, integrates financial expertise with data engineering to help buyers quantify cyber risks in dollar terms. By addressing these risks upfront, buyers can ensure security issues are properly accounted for in valuation models and deal structures.
2. Legal and Regulatory Penalties
When you acquire a company, you’re not just taking on its assets - you’re also inheriting its legal baggage. If the company has experienced any data breaches or security violations before the acquisition, those liabilities become yours. This means fines, lawsuits, and regulatory actions could come your way, even if those issues weren’t disclosed during the negotiation process. It’s an automatic transfer of responsibility, underscoring the importance of thorough due diligence in every M&A transaction.
Take the Verizon-Yahoo! deal in 2017 as an example. After acquiring Yahoo!, Verizon uncovered massive, previously undisclosed breaches that affected 3 billion user accounts. The consequences were severe: a $350 million reduction in the purchase price, $35 million in SEC fraud penalties for Yahoo! due to nondisclosure, and $80 million in lawsuits from stakeholders [8]. For Verizon, this meant years of legal headaches and damage to its reputation - all stemming from incidents that occurred before the merger.
In the U.S., laws like the CCPA enforce strict compliance, while cross-border acquisitions must also adhere to regulations like the GDPR [2]. Regulators don’t care whether a breach happened before or after the acquisition - the new owner is held accountable for all inherited cybersecurity lapses.
The scale of this risk is alarming. A report by Forescout revealed that 53% of M&A professionals encountered major cybersecurity issues that threatened their deals [2]. Additionally, more than 33% of firms reported experiencing new breaches during the integration process [7].
To mitigate these risks, you need to take compliance checks seriously. Conduct forensic analyses and compliance audits as part of your due diligence. Scrutinize the target company’s breach history, regulatory filings, and any ongoing investigations. Push for full disclosure of past security incidents and negotiate indemnities to protect yourself. Failing to do so could leave you with what some experts call "cyber grenades" - hidden legal liabilities that explode long after the deal is finalized [2][6].
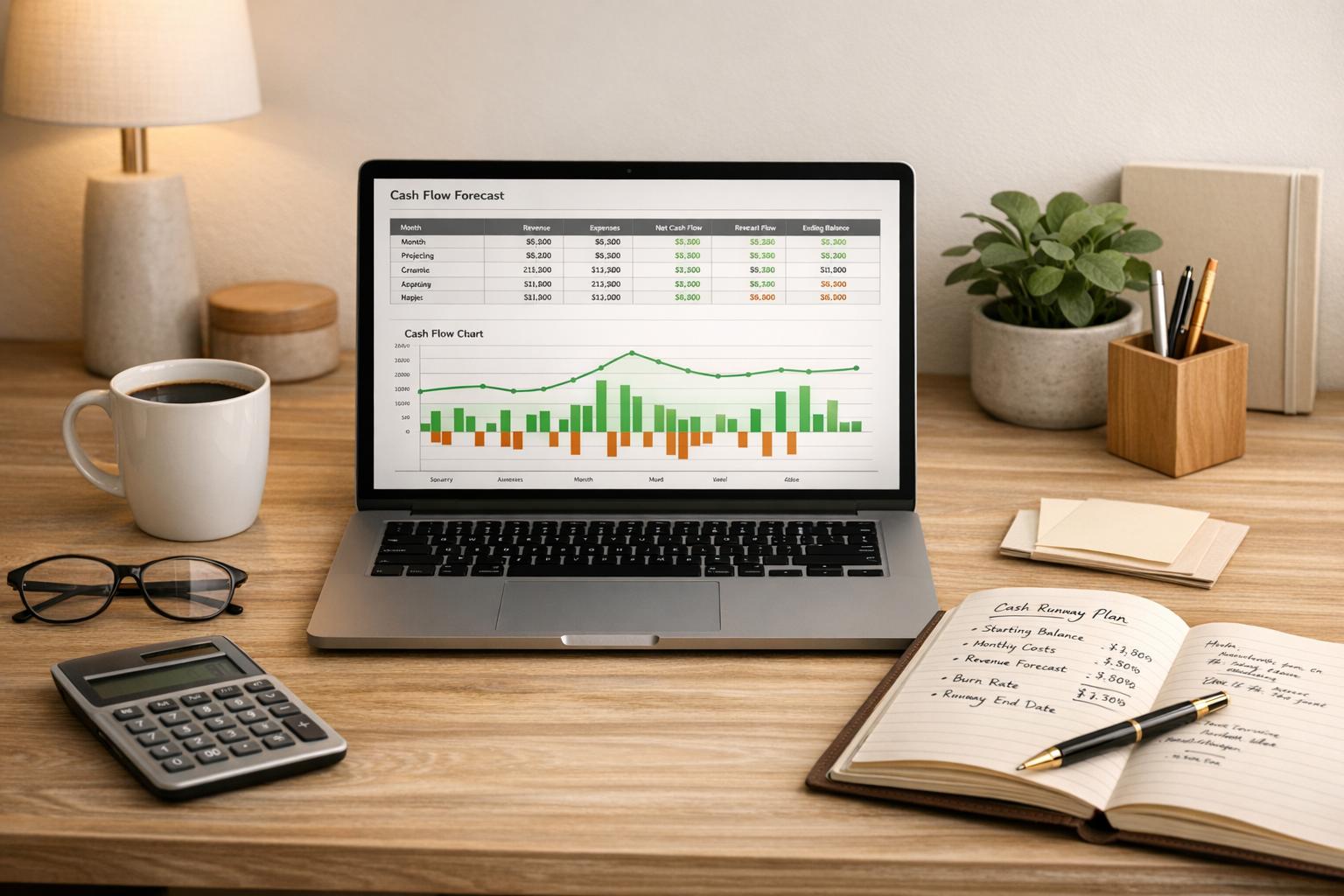
3. Unexpected Integration Costs
Security issues that arise after closing a deal can quickly drive up integration costs, eating into the benefits you expected to gain. These hidden expenses can add up fast.
For instance, a data breach could require immediate incident response and forensic investigations, which often come with hefty professional fees - sometimes reaching into the hundreds of thousands of dollars. On top of that, you may need to invest in critical upgrades, such as phasing out unsupported systems, replacing outdated applications, implementing multi-factor authentication, or deploying modern security tools. For U.S. mid-market transactions, fully updating an acquired company's security infrastructure can cost millions over a 12 to 24-month period[1][5].
Sometimes, security vulnerabilities might force you to keep the acquired company's systems on separate networks until a full risk assessment and remediation plan is completed. This isolation can delay essential integration tasks like consolidating Active Directory, enabling single sign-on, migrating email systems, or integrating ERP and CRM platforms[3]. These delays not only slow down the overall integration process but also rack up ongoing costs, such as paying for duplicate software licenses, overlapping vendor contracts, and redundant staffing.
To manage these rising costs, it's crucial to plan ahead during the due diligence phase. Allocate a specific cyber risk integration budget with detailed line items for remediation projects, security subscriptions, consultant fees, and a contingency reserve of 10–20% to handle unforeseen expenses[1]. Firms like Phoenix Strategy Group can help translate technical findings into practical financial models and budgets, helping you avoid unpleasant surprises after the deal closes.
sbb-itb-e766981
4. Brand Damage and Customer Loss
When data breaches occur during or after M&A transactions, they can severely harm the reputation of the merged company. Such incidents send a clear message to customers, partners, and investors about potential security failings. For customers, the knowledge that their data has been compromised often leads to a loss of trust. This is especially damaging in the U.S., where concerns about identity theft, payment card fraud, and misuse of personal information are particularly high[2][4].
The fallout doesn't stop at trust issues. Losing customers means losing recurring revenue, opportunities for cross-selling, and the foundation of strong customer retention[1][5]. Sales teams often face longer deal cycles and higher rejection rates as formal vendor risk reviews highlight security concerns. Alarmingly, 73% of M&A respondents in one survey stated that an undisclosed data breach would immediately terminate a deal[2]. These financial hits only add to the challenges of integrating two companies.
The damage also extends to public perception. Negative press from breach notifications and regulatory findings can dominate media cycles, casting the acquiring company in a poor light[3][4]. This kind of coverage can lower brand sentiment, complicate efforts to close new deals, and even affect equity valuation and future funding costs[1][4]. Management teams often find themselves distracted from crucial integration tasks - like aligning brands and launching marketing efforts - as they shift focus to crisis management and damage control[1][3].
To protect brand equity, proactive cyber due diligence is essential. Conducting comprehensive security audits and reviewing past incidents before finalizing the deal can help mitigate risks[1][3]. Monitoring metrics like customer churn, net promoter scores, complaint rates, and deals lost due to security concerns provides a clearer picture of reputational damage[2][4]. Firms like Phoenix Strategy Group specialize in incorporating cyber-risk assessments into valuation models, ensuring that brand and customer impacts are evaluated alongside technical and legal considerations[1][5].
5. Outdated Systems and Third-Party Weaknesses
When companies are acquired, they often bring along outdated systems that can be a ticking time bomb for cybersecurity. These systems might run on unpatched software, rely on unsupported infrastructure, or lack modern encryption standards. Without regular updates, they leave the door wide open for cybercriminals to exploit known vulnerabilities. In fact, a survey revealed that 53% of respondents encountered cybersecurity issues stemming from outdated or vulnerable systems, jeopardizing M&A deals in the process [2]. These risks don’t just pose immediate threats - they can also create long-term problems that surface during system integration.
The danger becomes even more pronounced if attackers have already compromised these environments before the deal. Dormant advanced persistent threats (APTs) in outdated systems can spring to life during the integration phase [6]. Take the 2022 Change Healthcare-UnitedHealth Group merger as an example. A ransomware attack exploited weaknesses in inherited systems post-acquisition, exposing the data of over 100 million individuals and causing billions of dollars in damages [2].
Adding to the complexity are third-party vendor relationships. Many acquired companies maintain partnerships with vendors that have weak cybersecurity measures, creating additional entry points for attackers. Research shows that 80% of global dealmakers uncovered data security issues, including third-party vulnerabilities, in at least 25% of M&A targets over a two-year period [9].
Integration itself can also introduce risks when security practices between the two companies don’t align. For instance, one firm might use multifactor authentication while the other relies on basic passwords, creating security gaps [6]. More than one-third of cybersecurity professionals report that their organizations experienced breaches tied to M&A integration activities [7]. If acquired systems aren’t isolated and thoroughly scanned for vulnerabilities before being connected, these issues can lead to breaches, regulatory fines, and operational disruptions long after the deal is finalized.
To address these challenges, acquirers must take proactive steps during due diligence. This includes conducting network testing, security audits, and detailed third-party risk assessments. Mapping out vendor relationships and ensuring systems are up-to-date before closing can help identify and mitigate inherited risks [1][3].
How to Reduce M&A Security Risks
Addressing cybersecurity risks during M&A transactions requires proactive steps at every stage of the process. Start by embedding cybersecurity assessments alongside financial and legal due diligence. This means identifying critical systems and sensitive data - like customer personally identifiable information (PII), payment details, intellectual property, and trade secrets - and mapping how this data moves within the organization. Investigate any past or ongoing security incidents, including undisclosed breaches, and evaluate the effectiveness of remediation efforts. Examine the target company's security governance, including policies, roles, budgets, and adherence to frameworks like NIST CSF or ISO 27001. Conduct technical evaluations such as vulnerability scans, penetration testing, and configuration reviews for endpoints, servers, cloud environments, and identity systems. These findings should directly inform the financial terms of the deal [1][2][3][5].
Translate technical audit results into measurable financial impacts. For instance, if outdated systems or regulatory risks are uncovered, calculate the associated costs in U.S. dollars and incorporate these into valuation adjustments, escrow holdbacks, or extended indemnities. Use industry benchmarks to estimate potential exposure and negotiate protections such as representations, warranties, or specialized cyber insurance. Many U.S. companies now rely on cross-functional cyber diligence teams, bringing together experts from security, legal, finance, and operations to quickly interpret findings and adjust deal terms accordingly [2][5].
Once the deal is finalized, isolate the acquired systems before integration. Implement strict network segmentation and enforce access controls, including multifactor authentication and updated identity management protocols. Deploy endpoint protection tools, extended detection and response (EDR) systems, and centralized logging to monitor the new environment. Conduct threat hunts to identify dormant malware or advanced persistent threats (APTs) that may have existed pre-acquisition. Delay high-risk integrations - like directory trusts, email migrations, or consolidating ERP and CRM systems - until a thorough risk assessment and remediation plan is completed [3][4][5].
For inherited risks tied to third-party vendors and legacy systems, begin with a detailed inventory of outdated applications, unsupported operating systems, and vendor relationships. Rank each based on factors like internet exposure, data sensitivity, and business importance. For high-risk legacy systems, decide whether to decommission them, migrate data to secure platforms, or implement segmentation with compensating controls like virtual patching. Review vendor contracts for security requirements, incident notification timelines, and audit rights. Use security questionnaires and SOC 2 reports to evaluate vendors, and terminate or replace those that fail to meet minimum standards. Address all identified risks and legacy issues with immediate and precise financial and technical solutions [4][5].
Engaging experienced advisors can help convert cyber risks into actionable deal terms. Phoenix Strategy Group specializes in integrating cybersecurity into M&A strategies. They assist companies by designing secure data architectures for post-deal integration, implementing data warehouses with strict access controls, and streamlining overlapping systems to reduce both cyber risks and IT expenses. Additionally, their fractional CFO and FP&A services ensure that cyber remediation and integration projects align with financial goals, helping management prioritize efforts that deliver tangible risk reduction and return on investment in the U.S. market.
Conclusion
Data security breaches present five major risks that can derail M&A transactions: inaccurate company valuation when hidden vulnerabilities come to light, legal and regulatory penalties from exposed customer or payment data, unexpected integration costs tied to emergency fixes, brand damage and customer attrition that weaken the revenue base being acquired, and outdated systems or third-party vulnerabilities that introduce long-term risks into the merged entity.
More than 70% of dealmakers view undisclosed breaches as deal breakers, with many only uncovering these risks after the deal closes [2]. For instance, undisclosed breaches have previously forced significant reductions in purchase prices [8]. A more recent example is the ransomware attack on Change Healthcare after its acquisition by UnitedHealth Group, which resulted in substantial financial losses and widespread data exposure [2].
These risks highlight the importance of thorough cyber due diligence. Buyers inherit the target company’s full cyber risk profile, including any undisclosed breaches, regulatory violations, and legacy vulnerabilities. This isn't just an IT issue - it’s a financial and reputational liability. Considering that the average data breach costs $4–5 million and regulatory bodies now expect proactive oversight, ignoring cyber diligence is a serious fiduciary risk [4][5].
Incorporating cybersecurity assessments early in the process - such as mapping sensitive data, reviewing breach histories, and evaluating vendor risks - can lead to practical safeguards like price adjustments, indemnities, and phased integrations. These strategies help control costs and protect the value of the deal. For growth-stage U.S. companies navigating M&A, partnering with advisors skilled in both financial modeling and data security can make a significant difference. Phoenix Strategy Group specializes in integrating cyber risk into deal models, aligning remediation efforts with financial objectives, and creating secure data systems for post-deal integration, ensuring that cybersecurity enhances rather than undermines transaction value.
Cybersecurity is no longer just a back-office concern - it’s a critical deal risk that requires the same level of scrutiny as any other material liability. Address it with the seriousness it deserves, and bring in specialized expertise early to safeguard both the transaction and your long-term enterprise value.
FAQs
What steps can companies take to uncover hidden data breaches before finalizing a merger or acquisition?
Before finalizing a merger or acquisition, it's crucial to dig deep into the cybersecurity landscape of the target company. This means conducting detailed due diligence, which should include security audits, vulnerability checks, and a close examination of data access logs to spot any suspicious activity.
Using advanced data analysis tools to pinpoint anomalies can be a game-changer in identifying hidden breaches. Tackling these risks head-on ensures that your investment is protected and helps you steer clear of unexpected and expensive problems after the deal is done.
How can companies reduce legal risks from data breaches during M&A?
When navigating mergers and acquisitions, reducing legal risks tied to inherited data breaches starts with thorough due diligence. This process helps uncover existing vulnerabilities or any past incidents that could pose a threat. If a breach is discovered, notify impacted parties right away - prompt action not only demonstrates good faith but also shows compliance with relevant regulations.
Keep a detailed record of every step taken to address the issue, from updating security protocols to implementing remediation measures. It’s also wise to work closely with legal professionals to ensure your response aligns with both federal and state data breach laws. This approach can help limit liabilities and safeguard your organization’s reputation.
What are the cybersecurity risks of using outdated systems during M&A integrations?
Outdated systems can pose major cybersecurity threats during mergers and acquisitions, creating exploitable gaps for hackers. Without essential updates and patches, these systems become easy targets for breaches, unauthorized access, and even data theft.
Additionally, they hinder real-time monitoring and compliance with current security standards, which could lead to regulatory penalties and harm a company's reputation. Tackling these security weaknesses early in the M&A process is critical to ensuring a smooth and secure integration.