PCI DSS for SaaS Companies

Handling payment card data? You need PCI DSS compliance. SaaS companies must secure cardholder data to meet the Payment Card Industry Data Security Standard (PCI DSS). This applies if you store, process, or transmit card data - or even indirectly impact it. Noncompliance risks fines, customer loss, and inability to process payments.
Key points to know:
- Merchant vs. Service Provider Roles: Your responsibilities depend on whether you handle payments for your services or enable payments for customers.
- PCI DSS v4.0 Updates: New requirements include multi-factor authentication, stronger password policies, and enhanced phishing protections.
- Reducing Scope: Use tokenization, hosted payment pages, or PCI-compliant gateways to limit your exposure.
- Cloud Compliance: Even with cloud providers, you’re responsible for securing application layers and managing access controls.
PCI DSS compliance isn’t just about avoiding penalties - it builds trust, shortens sales cycles, and opens doors to enterprise deals. Start by mapping your cardholder data flows, defining your Cardholder Data Environment (CDE), and addressing compliance gaps.
PCI 4.0: A Simple Checklist of the PCI DSS 4.0 Requirements
Determining PCI DSS Scope for SaaS Companies
PCI DSS Payment Integration Methods and Compliance Scope for SaaS
Defining the Cardholder Data Environment (CDE)
The Cardholder Data Environment (CDE) is at the heart of your PCI DSS scope. It includes every system that stores, processes, or transmits cardholder data, as well as any system that could impact the security of those components [3]. For SaaS companies, this often means databases, APIs, admin consoles, CI/CD pipelines, and any other systems interacting with payment card data.
To start, map out your data flows. This means identifying where cardholder data enters your system and tracking its movement through application backends, message queues, databases, caches, logs, backups, analytics platforms, or data lakes. A common pitfall for SaaS companies is unintentionally expanding their scope - like when Primary Account Numbers (PANs) end up in logs or error traces.
For multi-tenant architectures, isolation is key. Implement controls to ensure one customer cannot access another's cardholder data. Clearly document which microservices handle raw card data and which process tokens. Define the network segments or security groups that separate your CDE from other systems.
Using network segmentation can help reduce both scope and costs. This can be done by isolating CDE systems with Virtual Private Clouds (VPCs), subnets, or security groups. Additionally, keeping updated diagrams of your CDE - covering network layout, data flows, and cloud architecture - is critical. Qualified Security Assessors (QSAs) will expect thorough and accurate documentation.
Once your CDE is clearly defined, the next step is to evaluate how your payment integration methods affect your scope.
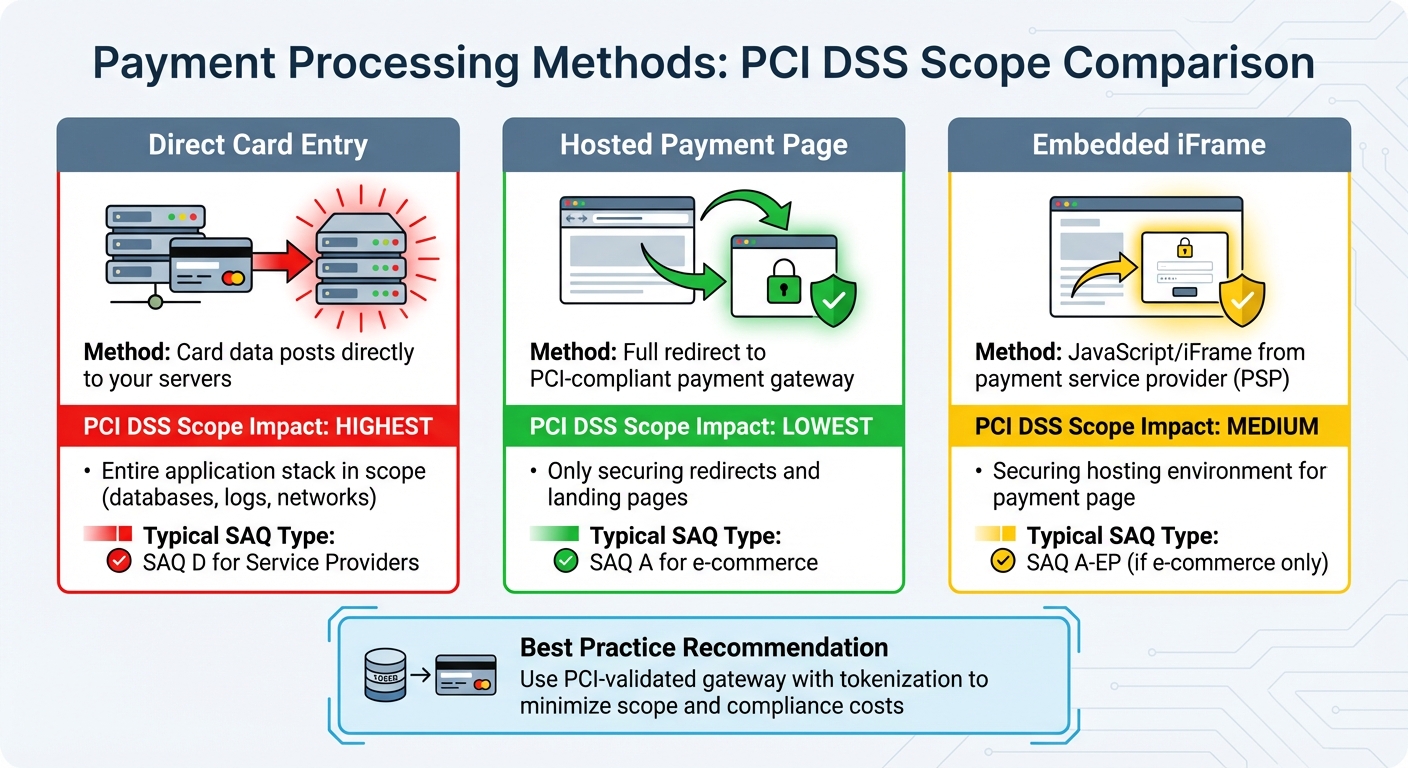
Payment Processing Methods in SaaS
The way your SaaS platform handles payments has a direct impact on your PCI DSS scope and the complexity of your compliance efforts. Here are three common integration patterns, each with varying levels of scope and audit requirements:
| Integration Pattern | PCI DSS Scope Impact | Typical SAQ Type |
|---|---|---|
| Direct card entry into your SaaS app (card data posts to your servers) | The entire application stack, including databases, logs, and connected networks, is in scope, resulting in the largest audit surface. | SAQ D for Service Providers |
| Hosted payment page / full redirect to a PCI-compliant payment gateway | Your platform avoids handling card data directly, limiting scope to securing redirects and landing pages. | SAQ A for e-commerce |
| Embedded iFrame / JavaScript from the payment service provider (PSP) | Scope focuses on securing the hosting environment for the payment page, such as web servers and scripts. | SAQ A-EP (if e-commerce only) |
To simplify compliance, consider using a PCI-validated gateway with tokenization. Configure your billing system to rely only on tokens and customer IDs rather than storing PANs. This approach not only streamlines your CDE but also helps make annual PCI compliance costs more predictable.
Be cautious with third-party scripts and support tools to ensure they do not inadvertently capture cardholder data.
Cloud Models and Shared Responsibility
After defining your CDE and understanding how payment integrations affect your scope, it’s time to evaluate how your cloud deployment model influences your PCI DSS responsibilities.
Your choice of cloud model determines how compliance duties are divided between you and your infrastructure provider. In a public cloud (IaaS) setup, the provider is responsible for securing the physical infrastructure - like data centers, core networking, and hypervisors - and typically provides an Attestation of Compliance (AOC). However, you remain accountable for securing everything within the cloud, including network segmentation, operating systems, patching, access controls, key management, logging, and application security for all in-scope workloads.
To stay compliant, identify which cloud resources are part of your CDE and enforce PCI-grade security measures such as firewalls, encryption, multi-factor authentication (MFA), and monitoring. Additionally, PCI DSS requires you to manage third-party providers, including your cloud vendor, through contracts, service-level agreements (SLAs), and regular reviews.
In private cloud or on-premises environments, your organization takes on a greater share of PCI responsibilities. This includes managing physical facilities, hardware, storage, networking, operating systems, middleware, and applications for CDE components. While this approach may increase compliance costs due to staffing and tooling needs, it offers more control, predictable performance, and customization options for clients with strict requirements around data residency.
Platform-as-a-Service (PaaS) strikes a balance between the two. The provider handles the underlying platform, while you focus on securing your applications, managing identities, protecting data, and configuring systems securely. Regardless of the model, remember that outsourcing infrastructure doesn’t mean outsourcing accountability. QSAs will review both your provider’s AOC and your internal configurations and procedures to ensure all PCI requirements are met within your scoped environment.
Core PCI DSS Requirements for SaaS Companies
After defining your scope and cloud model, the next step is translating PCI DSS requirements into actionable controls. These 12 core requirements apply to any organization handling payment card data, but for SaaS companies operating in cloud environments, they focus on areas like network security, data protection, and secure development practices.
SaaS platforms face unique challenges in implementing these controls, especially in distributed, multi-tenant cloud setups without traditional perimeters. Instead of relying on physical firewalls or on-site data centers, your team needs to think in terms of microsegmentation, identity-based access controls, and continuous monitoring.
According to IBM's 2024 report, the average cost of a data breach globally is $4.45 million. Non-compliance penalties for SaaS companies can range from $5,000 to $100,000 per month, along with increased transaction fees and potential termination of processing agreements.
The upside? Cloud-native tools like security groups, IAM roles, and centralized logging align well with PCI DSS controls. The challenge lies in configuring them properly and maintaining thorough documentation for auditors.
Network Security in Cloud Environments
While network security in the cloud differs from traditional setups, the core principle remains: limit access to only what’s necessary. For PCI DSS Requirement 1, which mandates firewalls to protect cardholder data, cloud environments rely on virtual firewalls, security groups, network ACLs, and VPC configurations.
- Configure security groups to allow traffic only on required ports and protocols. For example, if your payment service only needs to connect with your database and a specific gateway, the rules should reflect that - no more, no less.
- Use microsegmentation to ensure that even within your Cardholder Data Environment (CDE), services can only access the specific resources they need.
Administrative access also requires robust safeguards. Use jump hosts or bastion services for production systems and enforce multi-factor authentication (MFA) for all administrative access, including cloud consoles, CI/CD tools, and production databases. PCI DSS v4.0 explicitly requires consistent MFA enforcement, and auditors will check compliance.
To protect against web-based attacks like SQL injection and cross-site scripting (XSS), deploy Web Application Firewalls (WAFs) and Intrusion Detection/Prevention Systems (IDS/IPS) at the application’s edge. Managed WAF services offered by cloud providers can integrate directly with load balancers and API gateways for streamlined protection.
For third-party integrations - such as payment gateways or analytics tools - treat them as part of your PCI scope if they interact with cardholder data. Review each vendor's PCI DSS Attestation of Compliance (AOC), restrict connectivity to approved endpoints, enforce TLS 1.2 or higher for all API communications, and monitor API traffic for anomalies. If your SaaS platform uses JavaScript widgets or embedded scripts on payment pages, inventory all third-party scripts and apply Content Security Policy (CSP) headers to block unauthorized code execution.
Once your network security controls are in place, the next step is ensuring robust data protection.
Data Encryption and Tokenization
Encryption and tokenization are critical for protecting cardholder data and meeting PCI DSS Requirements 3 and 4. These standards require encrypting data both in transit and at rest, but the best approach for SaaS companies is to avoid storing raw cardholder data altogether.
- For data in transit, use TLS 1.2 or higher with strong cipher suites for all connections transmitting cardholder data. This includes not only internet-facing endpoints but also internal APIs and microservices. Disable weak protocols like SSL, enable HTTP Strict Transport Security (HSTS) to prevent downgrade attacks, and automate certificate management to avoid expired certificates.
- For data at rest, encrypt storage using robust algorithms like AES-256. This applies to databases, backups, object storage, and logs. Rotate encryption keys annually or when personnel with access leave the organization. Implement split-knowledge and dual-control for key management to prevent any single individual from accessing both the encrypted data and its decryption keys.
The most effective way to reduce PCI scope is through tokenization. Design your architecture so payment details are sent directly from the client (browser or mobile app) to a PCI-compliant payment gateway like Stripe, Braintree, or Adyen. These gateways return a token that your SaaS platform can store and use for future transactions. Since only the gateway can map tokens back to actual Primary Account Numbers (PANs), even if your database is compromised, the risk is minimal.
If storing PANs is unavoidable, limit storage to truncated PANs (e.g., last four digits) and enforce strict access controls and logging for systems handling full PANs. Use data discovery tools to ensure cardholder data doesn’t unintentionally end up in logs, analytics platforms, or customer support systems - common pitfalls that can unexpectedly expand your PCI scope.
Once data protection is addressed, focus on securing your application development process.
Secure Application Development
PCI DSS mandates secure development practices, which means integrating security into every phase of your Software Development Life Cycle (SDLC). For SaaS teams operating in continuous deployment environments, this requires embedding security checks directly into CI/CD pipelines.
- Follow OWASP secure coding standards and provide annual developer training on secure payment practices.
- Integrate Static Application Security Testing (SAST) and Software Composition Analysis (SCA) into CI/CD pipelines to detect vulnerabilities in code and third-party dependencies. Block builds with critical vulnerabilities until they’re resolved.
- Conduct code reviews for high-risk changes, such as those involving authentication, payment processing, or cryptography. Document these reviews and maintain audit trails. This also applies to infrastructure-as-code templates like Terraform or CloudFormation - scan for misconfigurations that could violate PCI controls, such as open security groups or unencrypted storage.
Regular testing is equally important. Perform penetration tests at least annually and after major changes, focusing on payment pages, APIs, and admin portals. These tests should cover network, application, and API layers, addressing modern threats like credential stuffing and API abuse. Remediate high-risk findings promptly and retest to confirm fixes.
Run authenticated vulnerability scans quarterly and after significant updates. Use an Approved Scanning Vendor (ASV) where required, and prioritize patching based on risk. For example, critical vulnerabilities should be patched within 30 days. Automate patch pipelines for operating systems, containers, and third-party components to streamline this process.
Lastly, ensure non-production environments (development, testing, staging) never contain real cardholder data. Use synthetic or anonymized datasets for testing and tightly control access between environments to prevent insecure configurations from being promoted to production.
sbb-itb-e766981
How to Achieve PCI DSS Compliance
Achieving PCI DSS compliance isn’t a one-and-done task - it’s an ongoing effort. It starts with understanding what needs protection, identifying gaps, and building systems to stay compliant throughout the year. For SaaS companies, the process revolves around three main areas: accurate scoping and gap analysis, establishing a secure infrastructure, and maintaining thorough documentation to demonstrate compliance.
Cloud-native setups can meet PCI requirements if the 12 controls are properly applied and supported by clear evidence.
Scoping and Gap Analysis
This step ensures all components involved in handling cardholder data are accurately identified and classified.
Start by mapping out all assets and workflows interacting with cardholder data. This includes your production application, databases, monitoring tools, CI/CD pipelines, third-party APIs, support systems, and embedded payment page components. Create detailed data flow diagrams that show where cardholder data enters, how it moves through various systems (such as web apps, mobile SDKs, billing portals, servers, and payment gateways), and where tokenization occurs.
In cloud-based environments, connect these flows to specific services like VPCs, subnets, containers, serverless functions, or storage buckets. Clearly define your Cardholder Data Environment (CDE) and any systems linked to it. Classify each component as in-scope, connected-to-CDE, or out-of-scope, and aim to reduce the scope by segmenting or redesigning systems to move them out of the CDE wherever possible.
Reducing scope is a game-changer. Many SaaS companies achieve this by using PCI-compliant payment gateways with hosted payment pages or iFrames, allowing raw card data to bypass their servers entirely. Tokenization is another effective method to shrink the scope.
Once your scope is finalized, conduct a gap analysis against PCI DSS v4.0’s 12 requirements. Document the implementation status of each control, including supporting evidence like configurations, screenshots, and policies. Prioritize gaps based on risk and remediation effort, focusing on measures that secure cardholder data (such as strong authentication, encryption, network segmentation, and logging) and those with new or strict deadlines under v4.0.
Building a PCI-Compliant Security Infrastructure
After defining your scope and identifying gaps, the next step is configuring your cloud infrastructure to meet PCI standards.
This involves aligning your cloud security tools, such as security groups, IAM roles, encryption services, and logging platforms, with PCI requirements. Document these configurations to prepare for audits.
For network security, use virtual firewalls, security groups, network access controls, and VPC setups to limit traffic to CDE components. You can implement microsegmentation through per-service security groups or service meshes and deploy a Web Application Firewall (WAF) for internet-facing applications. For encryption and key management, enforce TLS 1.2 or higher for data in transit, disable weak ciphers, and encrypt stored cardholder data using strong algorithms managed through HSMs or cloud key management services. Ensure strict access controls and regular key rotation.
Identity and access management is equally critical. Require multi-factor authentication (MFA) for administrative access to cloud consoles, CI/CD tools, production databases, and support systems, as well as for any access to the CDE. Use role-based access control (RBAC) and the principle of least privilege, and conduct quarterly reviews to remove unnecessary privileges.
Operationally, set up centralized logging and monitoring for all systems within the CDE. Capture API calls, authentication events, configuration changes, and firewall or WAF logs, and establish alerts for suspicious activity. Perform internal vulnerability scans monthly, schedule quarterly scans with an Approved Scanning Vendor (ASV), and track remediation efforts systematically.
Documentation and Ongoing Compliance
Keeping detailed records of your controls is essential for passing PCI audits.
Your documentation should include security policies, network and data flow diagrams for the CDE, procedures for change management and incident response, vendor management processes, and coding/testing standards. These records must reflect your actual operations and demonstrate that controls are continuously in place.
Maintain evidence such as quarterly ASV scan reports, internal vulnerability scans, MFA configurations, firewall rules, logging settings, training records, and examples of access reviews or incident handling. Many SaaS companies use compliance tools and assign internal control owners to ensure logs, scans, and reviews happen on schedule rather than scrambling before an annual audit.
To stay organized, set up systems to collect and manage evidence, track metrics, and generate regular compliance reports. Align teams with clear KPIs and conduct regular reviews. Establish a continuous review cycle, with weekly tracking and monthly planning, to refine processes and address any gaps.
For SaaS companies in growth stages, integrating PCI compliance with broader business planning, budgeting, and vendor strategies can make the process more manageable. Phoenix Strategy Group offers advisory services to help align PCI documentation and metrics with broader audit, fundraising, or exit goals.
This approach to continuous compliance not only supports PCI requirements but also strengthens overall security and business operations.
Business and Financial Benefits of PCI DSS Compliance
PCI DSS compliance isn't just about meeting security standards - it's a smart investment that safeguards revenue, opens opportunities in new markets, and solidifies financial health. For SaaS businesses, the cost of achieving compliance is often far less than the potential losses from a data breach or losing critical enterprise contracts. Here’s a closer look at how compliance translates into cost savings, customer confidence, and aligned business goals.
PCI DSS Compliance Costs and Budgeting
The expenses tied to PCI DSS compliance fall into two categories: one-time project costs and recurring operational costs.
Initial Costs: These often include scoping and gap analysis with a Qualified Security Assessor (QSA), implementing security tools like web application firewalls, engineering work for remediation, and drafting policies and documentation.
Ongoing Costs: These cover periodic assessments, vulnerability scans, penetration testing, continuous monitoring, staff training, and ongoing security support.
For a small SaaS company using an outsourced payment gateway and managing a minimal Cardholder Data Environment (CDE), initial costs typically range from $10,000 to $50,000, with annual expenses between $5,000 and $25,000. Mid-sized SaaS firms with more complex systems may face upfront costs of $75,000 to $250,000 and annual costs of $50,000 to $150,000. Larger SaaS companies handling high transaction volumes may see initial investments exceeding $250,000, with yearly costs reaching six figures.
To reduce these expenses, many companies use tokenization and hosted payment pages from PCI-compliant gateways. This approach keeps raw card data out of their infrastructure, lowering both tooling and assessment costs. Additionally, aligning PCI investments with other frameworks like SOC 2 and ISO 27001 allows businesses to leverage a single set of controls for multiple certifications.
A typical three-year budget starts with higher project costs, gradually transitioning to steady operational spending. Companies should also plan for updates to PCI DSS v4.0 requirements and reserve funds for changes in architecture, new products, or evolving customer security needs. Automating evidence collection and using cloud-native security tools can further streamline costs as the business grows.
Building Customer Trust and Shortening Sales Cycles
PCI DSS compliance sends a clear signal: your platform meets rigorous card data security standards. For many U.S. mid-market and enterprise buyers - especially in industries like financial services, retail, and healthcare - this assurance is often a dealbreaker.
Having a Self-Assessment Questionnaire (SAQ) or Report on Compliance (ROC) ready early in the sales process can eliminate common vendor concerns, reassuring procurement and security teams that your platform won’t compromise their PCI obligations. This proactive approach can lead to larger deals, multi-year contracts, and quicker renewals.
Providing documentation of PCI compliance, evidence of regular vulnerability scans, and clear explanations of tokenization and encryption practices can streamline the sales process. In sectors like retail, where RFPs often require PCI attestations, being able to present these materials can turn a conditional opportunity into an immediate win. Beyond sales, demonstrating PCI compliance boosts confidence among board members and investors, showcasing your commitment to data security - a crucial factor during fundraising or exit planning.
Connecting Compliance with Business Goals
When done right, PCI compliance doesn’t just check a box - it drives business growth. SaaS companies that integrate compliance with their broader objectives often see it as a revenue enabler rather than an IT expense.
For example, PCI compliance can unlock access to regulated or security-sensitive markets, such as fintech or large retail chains, that demand robust security standards. A strong security posture reduces the risk of data breaches, improving customer satisfaction and renewal rates. Additionally, compliance can justify premium pricing for enterprise-grade or "regulated industry" versions of your product, meeting the heightened expectations of these markets.
The financial impact of non-compliance is significant. According to the IBM Cost of a Data Breach Report, the average cost of a data breach in the U.S. exceeds $9 million [1]. Merchants may also face costs of $50–$90 per compromised card, covering fraud, card reissuance, and fines [2]. PCI compliance helps mitigate these risks while improving sales performance.
Advisory firms like Phoenix Strategy Group play a key role in aligning PCI compliance with financial planning, fundraising, and M&A strategies. They offer services such as bookkeeping, fractional CFO support, and M&A advisory to quantify PCI investments in terms of predictable cash flow and revenue resilience. By comparing scenarios like “minimal compliance” versus “strategic security investment,” they help businesses understand the impact on margins, expenses, and enterprise value. During fundraising, they assist in presenting PCI compliance as a strength, linking it to stronger sales pipelines and reduced cyber risks. For M&A, they prepare diligence-ready materials - like PCI attestations and security roadmaps - reducing buyer concerns and potentially improving deal terms. By tying PCI compliance to financial and growth strategies, companies can maximize security investments for long-term success.
Conclusion
Key Takeaways for SaaS Companies
If your SaaS platform processes, stores, or even indirectly impacts cardholder data, PCI DSS v4.0 applies to you - even if you’re using a PCI-compliant payment gateway. To reduce your scope, consider tokenization, hosted payment pages, and PCI-compliant gateways to avoid handling raw card data directly. Remember, compliance isn’t a one-time task; it’s an ongoing process requiring regular risk assessments, quarterly scans, and constant monitoring.
Using cloud infrastructure doesn’t automatically make you compliant. Under the shared responsibility model, you’re still accountable for securing the application layer, managing access controls, and ensuring proper handling of cardholder data. To mitigate risks, enforce multi-factor authentication (MFA), apply least-privilege IAM policies, and encrypt data both in transit (TLS 1.2 or higher) and at rest. These steps not only minimize breach risks but also streamline vendor reviews and strengthen your position in fundraising or mergers and acquisitions.
| Theme | Key Takeaway for SaaS | PCI DSS v4.0 Angle |
|---|---|---|
| Scope & Applicability | Assume PCI applies if your SaaS impacts card data, and formally validate your scope. | Broader scope now includes more SaaS and service providers. |
| Risk of Non-Compliance | Breaches, fines, reputational harm, and payment processing bans are at stake. | Focus on ongoing risk management and testing. |
| Security-by-Design | Build PCI controls into your architecture and SDLC from the start. | Supports a tailored approach for cloud-native systems. |
| Continuous Program | Treat compliance as a continuous effort with scans, audits, and training. | Requires annual assessments, quarterly scans, and reviews. |
| Business Impact | Compliance boosts customer trust, facilitates larger deals, and simplifies due diligence. | Seen as a baseline for protecting cardholder data. |
These insights highlight the immediate steps SaaS companies can take to strengthen their compliance strategy.
Next Steps for Achieving Compliance
To kick off your PCI compliance journey, start by assigning ownership and mapping your payment data flows. Appoint a PCI owner - such as your CTO, CISO, or VP of Engineering - and schedule a scoped assessment within the next quarter. Within the next 30 days, focus on mapping payment data flows, defining your Cardholder Data Environment (CDE), determining your PCI level (SAQ vs. ROC), and conducting a gap analysis. Identify at least one quick win, such as enabling MFA for admin accounts, transitioning to a PCI-compliant gateway, or initiating a formal risk assessment.
Procrastinating on compliance can lead to rushed and expensive fixes later. Tackling it early and incrementally helps spread costs and reduces operational disruptions. If your team lacks the expertise, consider hiring a Qualified Security Assessor or an advisory firm like Phoenix Strategy Group. These experts can help align your compliance efforts with your financial planning, fundraising goals, and growth strategy - turning PCI compliance into a foundational element of your scale-up plan rather than a last-minute hurdle.
FAQs
How does PCI DSS v4.0 differ from earlier versions for SaaS companies?
PCI DSS v4.0 brings updated, more adaptable security controls, giving SaaS companies the freedom to implement solutions that suit their specific needs. A major focus is on a risk-based approach, which helps businesses target security efforts where they’re most needed, based on their unique vulnerabilities and potential threats.
Some of the key changes include stricter requirements for multi-factor authentication, updated encryption protocols, and better monitoring and logging practices. These updates aim to tackle emerging cybersecurity challenges while offering clearer instructions to help SaaS companies stay compliant in ever-changing environments.
What steps can SaaS companies take to minimize their PCI DSS compliance requirements?
SaaS companies can simplify their PCI DSS compliance efforts by leveraging tokenization and point-to-point encryption (P2PE). These technologies work by either replacing sensitive cardholder data with secure tokens or encrypting it during transmission. This approach keeps sensitive payment information out of your systems, significantly reducing the compliance workload.
Another smart move is to segregate payment card data from other systems. By isolating payment environments, you can narrow the scope of compliance requirements. Additionally, working with a trusted third-party payment processor can offload much of the responsibility for securing payment data. These providers are equipped to handle transactions securely, further easing your compliance obligations.
With these strategies, SaaS companies can keep their focus on business growth while ensuring a secure and compliant payment environment.
What should SaaS companies focus on to maintain PCI DSS compliance in cloud environments?
Maintaining PCI DSS compliance in cloud environments demands a focused and customized strategy. To start, strong access controls are crucial - they help restrict data exposure and ensure only authorized personnel can access sensitive information. Equally important is encrypting cardholder data, whether it's stored or being transmitted, to add an extra layer of protection. Don’t overlook the need for secure network configurations to shield critical data from potential threats.
Ongoing vigilance is key. Regularly monitor and test your cloud infrastructure to uncover vulnerabilities and address them promptly. At the same time, develop and enforce clear security policies tailored specifically to your cloud environment. These steps not only protect payment data but also reinforce customer trust in your organization's commitment to security.